Meltdown Bug aka Meltdown Attack For Intel Processors – What You Need To Know
What is the Meltdown bug?
Most of the bugs that make the news are software bugs, but the Meltdown bug is a hardware bug (in the form of a design flaw) that affects Intel processors going back several generations. In a nut shell, the Meltdown bug is a brand new way to (possibly) steal your information. Exploits were successfully tested on Intel CPU’s from the table below:
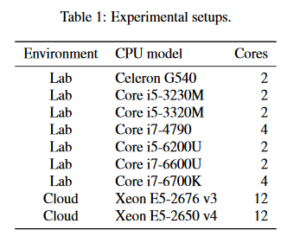
Meltdown bug exploits
The bottom line is that if Intel processors (including cloud based) run any of your operating systems or applications, you are potentially affected. The entire Meltdown bug white paper can be found here:
https://meltdownattack.com/meltdown.pdf
How bad is the Meltdown bug?
To us in cyber security, the Meltdown bug (aka a Meltdown attack) is a pretty big deal. However, CPU architecture is extremely complex, so this is not a huge surprise. Take a look at the CPU Protection Ring concept that is employed by nearly every modern CPU:
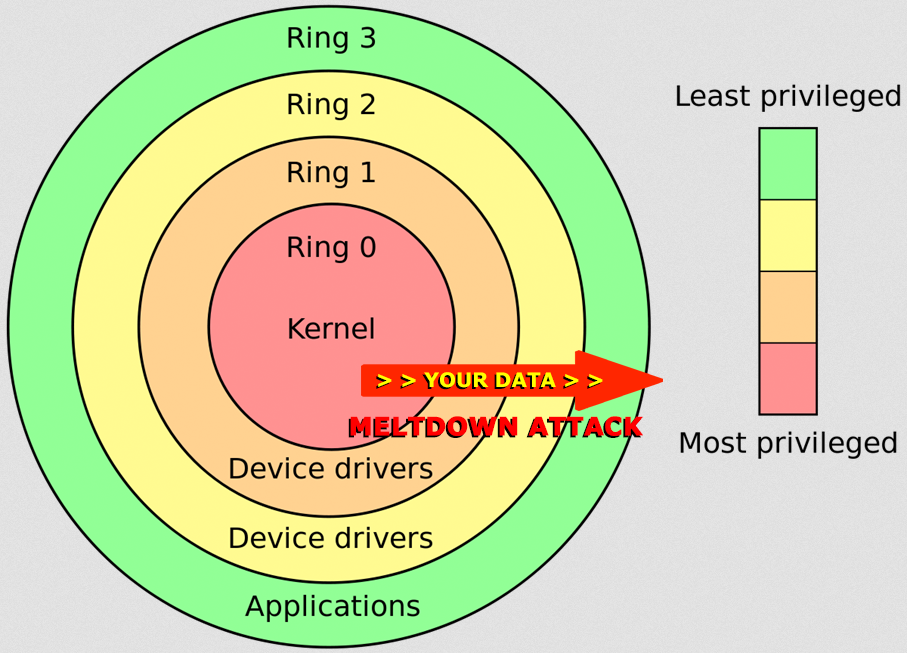
Meltdown Attack
In a Meltdown attack, a hacker can theoretically extract data from the red core to the green ring.
What should I do about the Meltdown bug?
Well, there is no evidence that the Meltdown bug impacts AMD processors – but then you’d be susceptible recently discovered Spectre bug, which we’ll be discussing in our next blog later today. You can always change your CPU out (and ask your cloud provider to do the same). Obviously this is not practical, but thankfully the researchers have already identified a fix, known as KAISER. All of the big tech companies such as Microsoft, Google, and Apple have either deployed fixes or will very soon – so keep a watchful eye out for software patches related to Meltdown.
Is there any good news here?
Yes. Firstly, the Meltdown attack is a theoretical attack that was discovered by security researchers, who notified vendors and CERT so that the flaw could be addressed. As of this writing, there is no evidence that the bad guys have used a Meltdown attack against anyone, or even have tools to do so.
What about the bad news?
The bad news is that since it is a hardware flaw, the Meltdown bug cannot really be “fixed”, only mitigated by software. Imagine that something made a small hole through your roof, letting light through – and you just replaced the roofing felt and the shingles over the hole. Your roof probably won’t leak, but the hole is still there. Also, like the KRACK bug, if state backed security services were aware of the Meltdown bug (very possible), it is highly likely they would sit on it instead of informing the public.
The Meltdown bug demonstrates once again why “Defense in Depth” is so important. Never assume that the security mechanisms protecting a piece of hardware or software are secure by themselves – real cyber security needs layers of defense.